What is an Incident Response Plan?
A comprehensive guide for executives and cyber‑leaders
In an era where cyber‑threats are escalating daily, from ransomware campaigns to insider breaches, supply‑chain attacks to software vulnerabilities – it’s no longer a question of if an incident will occur but when. That’s why having a robust, well‑documented Incident Response Plan (IRP) is essential to all organizations, regardless of size.
This blog explores what an IRP is, why it matters, how to build one, and answers key questions executives and leadership teams should ask.
What is an Incident Response Plan?
An Incident Response Plan (IRP) is a formal, documented strategy that outlines how your organization will detect, respond to, and recover from cyber OR information security events. It defines roles, responsibilities, processes, communication plans, and controls required to handle incidents from start to finish.
According to the National Institute of Standards and Technology (NIST), an IRP is the “documentation of a predetermined set of instructions or procedures to detect, respond to, and limit the consequences of malicious cyber attacks against an organization’s information system(s).”
This includes ransomware, data breaches, unauthorized access. But you may be surprised to learn that a good IRP should also address property damage with respect to physical security – such as a fire in a server room.
Similarly, the Cybersecurity and Infrastructure Security Agency (CISA) describes it as a written document, approved by senior leadership, to guide the organization before, during and after a confirmed or suspected security incident.
In short: an IRP turns chaos into coordination.
Why an IRP matters
1. Minimizes Impact & Accelerates Recovery
When an incident strikes, time is your enemy. A structured IRP means your teams don’t have to figure it out “on-the-fly.” Rapid detection, containment and recovery reduce operational, financial and reputational damage. For instance, organizations with documented IRPs identify and handle breaches substantially faster.
2. Supports Compliance & Audit Readiness
Many regulatory standards (e.g., PCI DSS, PHIPA, HIPAA, ISO 27001) require documented incident response capabilities. Having an IRP demonstrates governance and due‑diligence to auditors and regulators.
3. Builds Stakeholder Confidence
Customers, partners and boards expect you to have a dependable plan. Demonstrating readiness shows you take your risk exposure seriously.
4. Enables Continuous Improvement
An IRP isn’t a static document. It embeds a learning loop… review, revise, improve. Over time your organization becomes more resilient. The NIST lifecycle emphasizes this inclusive approach.
If you’re asking yourself, “what is an incident response plan?” – it’s essentially your roadmap for when the unexpected happens.
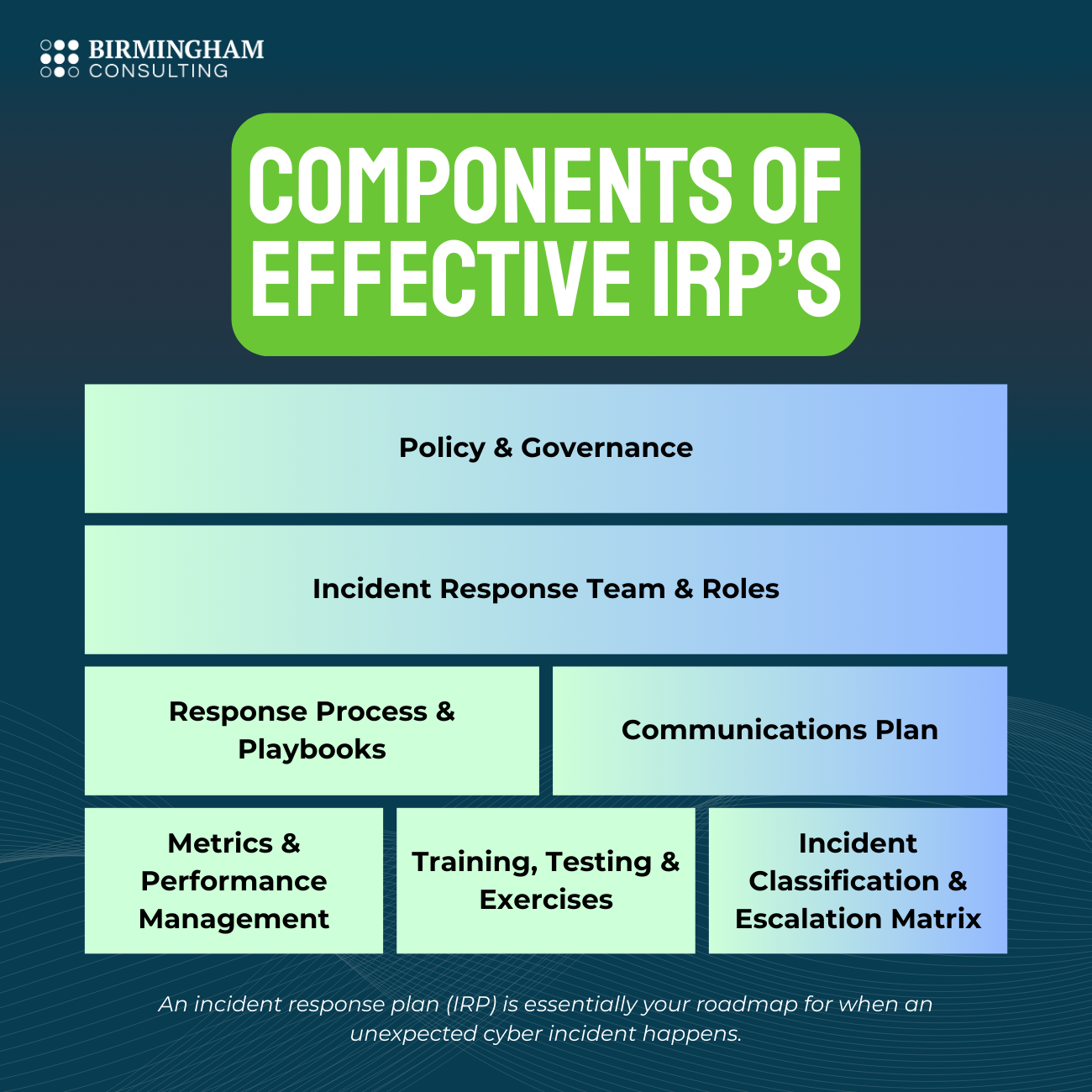
Key Components of an Effective IRP
Here are the building blocks of a resilient incident response plan.
A. Policy & Governance
- A high‑level policy approved by senior leadership that defines scope, objectives, approval authority, and triggers for activating the IRP.
- Alignment with corporate risk framework and cyber‑governance structure.
B. Incident Response Team & Roles
- Define a core team (e.g., Incident Manager, Technical Lead, Communications Lead).
- Extend roles to legal, HR, PR, business units, external forensic vendors.
- Document contact lists, escalation trees, backups and availability.
C. Incident Classification & Escalation Matrix
- Develop a risk classification matrix: severity levels (low/medium/high/critical), impact thresholds, business units affected.
- Consulting legal in particular, define what constitutes an “incident” vs a “security event” and triggers for activating the IRP.
D. Response Process & Playbooks
Your IRP should walk through the full lifecycle of incident response and include playbooks for common scenarios.
Four‑Phase Lifecycle (per NIST):
- Preparation – Policies, training, playbooks, tools.
- Detection & Analysis – Identify signs, confirm incident, assess scope.
- Containment, Eradication & Recovery – Stop impact spread, remove threat, restore operations.
- Post‑Incident Activity (Lessons Learned) – Review root causes, update plan, train.
Playbooks:
Standardized procedures for common incident types: ransomware, phishing, data breach, lost devices. These allow the response team to act quickly without reinventing the wheel.
E. Communications Plan
- Define internal and external communication protocols: who speaks to law enforcement, regulators, media?
- Outline tools (conference bridges, secure messaging), templates, timing, stakeholder lists.
F. Training, Testing & Exercises
- Conduct tabletop exercises (full simulations) at least annually or after major business/IT changes.
- Use the results to revise the IRP, identify gaps, and validate roles.
G. Metrics & Performance Management
- Track metrics such as MTTA (Mean Time to Acknowledge), MTTD (Mean Time to Detect), MTTC (Mean Time to Contain), MTTR (Mean Time to Recovery).
- Perform regular reviews of IRP performance and update accordingly.
How to Build Your Incident Response Plan: Step‑by‑Step
Here’s a practical roadmap for the leadership team to undertake.
Step 1 – Define Policy & Scope
Start at the top: Write an IRP policy, get executive sign‑off, link to business objectives. Clarify what systems and incidents are in scope.
Step 2 – Assemble the Team
Identify and document your core CSIRT (Computer Security Incident Response Team). Assign roles and backups. Ensure cross‑functional representation (IT, legal, business, communications).
Step 3 – Map the Incident Lifecycle & Build Playbooks
Draft your incident lifecycle phases aligned with NIST. For each common incident type (e.g., data breach, ransomware, insider threat), create a playbook with specific steps, roles, tools, communication flows.
Step 4 – Develop Communications Strategy
Document internal and external communications: who gets notified, when, and how. Pre‑prepare media holding statements and regulatory notification templates.
Step 5 – Conduct Training & Exercises
Run tabletop exercises– simulate scenarios, test team reaction, identify gaps. Periodically run full simulations with technical, legal and PR involvement.
Step 6 – Review, Measure & Improve
After each exercise (or real incident), hold a retrospective. Review team performance, controls used, communication flows. Update the IRP. Track metrics and review annually or when business/technology changes.
Step 7 – Maintain & Update
Your IRP should be a living document. Revise after organizational changes (mergers/acquisitions, new tech, regulatory shifts) and refresh training and playbooks accordingly.
FAQ’s – Common Questions about IRPs
Q1: Who should own the Incident Response Plan?
A: Ownership should reside with a senior executive (e.g., CISO or vCISO, or CIO). The incident manager leads the response during an event, but the IRP policy should be owned and approved at the executive level.
Q2: How often should an IRP be tested and updated?
A: At minimum, annually. Also after significant infrastructure changes, regulatory updates or after any major incident exercise.
Q3: Is an IRP only for cyber‑attacks?
A: No. While cyber‑incidents are a major driver, an IRP can cover any major disruptive event with respect to your security. For example, supply‑chain compromise, insider data theft, system outages, or physical security incidents (like a fire in your server room).
Q4: What metrics should we track?
A: Common metrics include MTTA, MTTD, MTTC, MTTR, SLA compliance, number of tests per year, and time to update the IRP after training/exercises.
Q5: What business units should be involved?
A: Besides IT/security, include legal/compliance, HR, communications/PR, business unit leads, risk management and external vendors/forensics in the policy development.
Q6: How do you store an incident response plan?
A: An IRP should always exist in both digital and hard-copy formats. While the digital version is convenient and easy to update, having a printed copy is essential in case your organization loses access to its IT networks or systems. Keep an up-to-date hard copy stored in a secure, but easily accessible, location.
Final Takeaways
An IRP is not a “nice‑to‑have” document. It’s a strategic imperative that translates governance into action when the unexpected happens. By documenting roles, processes and communications ahead of time, you gain clarity, speed, and control during an incident.
For executive leadership, the key questions are:
- Do we have a current IRP that has been approved and tested?
- Are our teams trained and aware of their roles?
- Are the lines of communication clear, including to external stakeholders (law‑enforcement, customers, regulators)?
- Do we review and update after every incident and major change?
By answering these, you’ll ensure your IRP truly delivers value. Not just as a document in the drawer, but as your organization’s roadmap to resilience.